Written by: Cory Goodman, Support Engineer
ATTENTION: If you are reading this article because you already have this virus, immediately shut down the infected computer and do not read this while on that machine.
The following article will describe the CryptoLocker and Cryptowall Viruses. Although there is a detailed description of what can be done, I highly recommend that you have a professional help you through the process of trying to recover your files if your computer is infected.
CryptoLocker is a virus that began making an appearance in September 2013. The virus CryptoLocker was taken down In Late May of 2014 through “Operation Tovar”. This team shut down the Gameover ZeuS botnet that had been used to distribute the CryptoLocker virus. The team recovered the private keys used in the encryption processes and a website, https://www.decryptcryptolocker.com/ , was created to help individuals who were affected by the virus to try and recover their files.
This same tool however, DOES NOT decrypt files for CryptoWall, which is the ongoing variant of CryptoLocker, still running rampant today.
CryptoWall is a virus that spawned from the ashes of Cryptolocker. Variants that were released include CryptoWall, CryptoWall 2.0, and CryptoWall 3.0. In this article we will focus on CryptoWall 3.0.
This virus encrypts commonly used data and files on your computer such as pictures, Word docs, Excel spreadsheets, pdf’s, pictures, music, etc.
- First it will make a copy of your original file and encrypt it with an RSA2048 key. Then it will delete the original files. It will continue doing this until it has encrypted all files on all disks and network shares the user can access.
- Second it will try to delete any Windows shadow copies of your files to prevent you from recovering any previous “unencrypted” versions of your files.
- During the encryption process the data in your files may look garbled, you may see an error message, and files you worked in recently will simply not open all of the sudden.
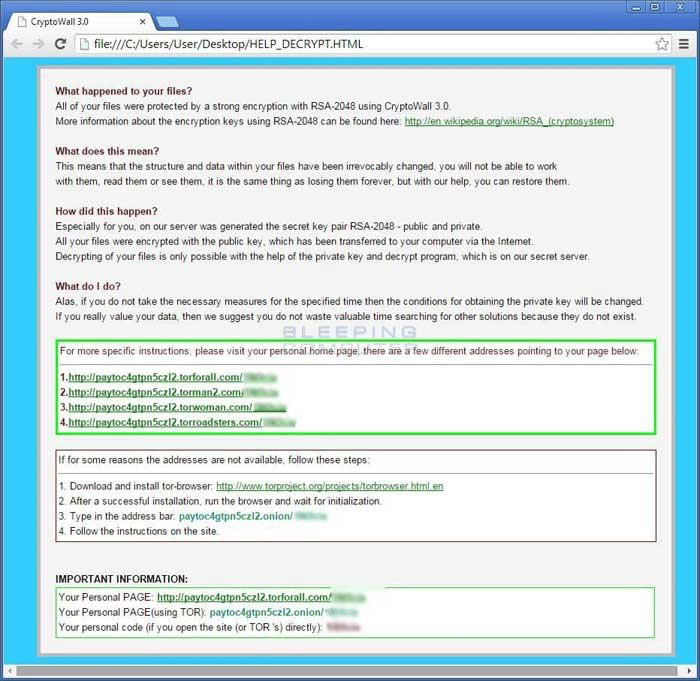
- After this process has completed you will get a pop-up ransom note that looks similar to the one below (an actual screenshot of an infected computer). You will also find DECRYPT_INSTRUCTION.HTML for CryptoWall 2.0 and HELP_DECRYPT.html files for CryptoWall 3.0 all throughout the file shares that were encrypted. (Please see the screenshot below.)
Screenshot of the ransom notice on an infected computer.
To understand how CryptoWall 3.0 functions let’s run through that process and look at a few key points. It makes a copy of your files, deletes the original and then deletes your Windows Shadow Copies. So what we learn here is:
- By deleting the original it opens up a possibility of recovering your data with drive recovery utilities
- By learning that Windows Shadow Copies are not deleted till the encryption process is actually complete you have a small window of opportunity to recover your data via Shadow Copies. But you have to shut your computer down the second you notice the virus to increase the likelihood of these recovery processes being able to work.
Recovering from the infection: So you have gotten the virus and are now dealing with it. Let’s figure out who is infected. If you are in a business environment with a server and are using Active Directory, the quickest way to figure out who it started from is by finding one of the HELP_DECRYPT.html files, right clicking it and going into its properties. You can then go to the details tab and see who created the file by looking at the Author or by whom it was last saved. This will give you a good start on which PC needs to be taken off the network. If you are in a home environment then you probably know it’s your PC.
If you have a backup after the PC has been isolated then you’re more than likely in better shape than most at this point. You can just get the machine wiped clean, reload with your operating system and restore from your backup.
Another option is to try cleaning Cryptowall 3.0 using utilities such as Malwarebytes, Combofix, Roguekiller and other utilities from Bleeping Computer using the following link.
https://www.bleepingcomputer.com/download/windows/security/ . But if for some reason the infection is not cleaned and you restore from backup, you may end up losing files all over again due to the infection. So most of the time it’s better to completely wipe and reload your machine from your Windows OS disk to cut down on the risk.
Trying to Recover from the infection with no backup: (The more common scenario)
The result of the following information is going to vary on a case by case basis and is not guaranteed to work. It’s simply a list of options than can be tried based on the nature of the virus.
(Note: I recommend the processes involved below be done by a Local IT Professional)
The virus invokes a two-step process to encrypt your files. If you were able to shut down your machine after the initial encryption, but before the shadow copies were deleted, you may still be able to recover your data.
To recover the shadow copies of your files you would need to boot your computer in Safe Mode with no networking. You do not want the infected machine talking to the Internet! In Windows Vista and Windows 7, Shadow Copies are normally turned on by default. Most of the time they are better known as previous versions. In Windows 8 and 8.1 previous versions were replaced by File History. This is normally turned off by default and needs to be configured.
Sometimes a third party utility needs to be used to access your computer shadow copies and in those cases you can use ShadowExplorer. With this utility, you get a slightly more simplified interface to restore your shadow copies.
If it’s already too late and no Shadow Copies are available from which to recover, you can try other Data Recovery Utilities such as Recuva, Recover My Files, Ontrack EasyRecovery, etc.
With these tools you may be able to recover the original deleted files from different sectors on the drive. You would want to remove the drive from the computer and hook it up to a secondary PC in a test environment to perform extended recovery in case of virus replication. You also want to make sure you minimize the read and writes being performed on that drive, so you have a better chance of recovering your data without it being overwritten in the cache. This is not a likely possibility of recovery, but it is a much better idea than paying the ransom.
After reading all of this you may be asking, “How do I protect myself against this virus?”
Well let’s go in order of importance:
- Backups: Make sure you have a reliable local and offsite backup. Local backups are great but USB drives can fail just as easily as your computer can. A backup that is stored in the cloud is offsite and may take longer to recover from, but will be worth having the knowledge that you can pull from it if you need it.
- Security in Business: Make sure you have a good firewall on the front end of your network; something that can scan traffic as it enters your network via an IPS Policy. We have our clients use Cyberoam Firewalls and have actually seen situations where the IPS policy in these firewalls prevented the initial encryption process from starting. You can read on Cyberoam’s website about how they are protecting people through IPS Policies.
https://www.cyberoam.com/blog/cryptowall-the-extended-version-of-cryptolocker/ - Centrally Managed Anti-virus: Aside from a front end firewall, make sure you have some sort of centrally managed antivirus installed on your server so you can find out who the infections are coming from. There is no guarantee an antivirus will stop this from infecting you, but it’s another active line of defense to help prevent this from happening.
- Security at Home: The above works in a business sense but you could just be a home user on your own and do not want to put out a large chunk of your money for something like a front-end hardware firewall. In this case, you still want a good antivirus to protect yourself but you may also want to look at CryptoMonitor by EasySync. Our good friends at bleepingcomputer.com have released an article talking about this utility. There is a Free version and a Pro version. The Free version gives you a frontline of security but may not be able to protect you in ways the Pro version can. The utility is fairly new but boasts a lot of potential. I went ahead and installed it on my PC and had no issues or problems with it. NOTE: This is NOT an Antivirus Software. It is a separate software to run alongside your current Antivirus Software as another line of defense. Here is the website for more information: https://www.easysyncsolutions.com/cryptomonitordetails.html
If all of this sounds confusing, you’re right. There is a lot to it, and there is the chance that your files may never be recovered. I strongly recommend that you take the precautions mentioned above to prevent getting the CryptoWall Virus in the first place. If you need help with that, call Nashville Computer. We can get you set up.
If you do get the virus, I also strongly recommend that you seek professional help instead of fighting it on your own. Professionals have the latest information, tools, and experience to help you.
If you would like help from Nashville Computer, Inc., give us a call at 615-864-9307.